Application of Data Proxies and Cognitive Firewalls to a Secure and Resource-Efficient Implementation for Connected Systems
The Inventors propose a technique for the secure and efficient implementation of connected systems via use of Data Proxies that approximate the state of a system with minimal resource inputs. Proxies abstract connectivity between applications and end devices, offering a chance to improve system security through the use of Cloud resources. This technology will enable connectivity to be deployed across more devices and larger networks including IoT systems, local area networks, and all other connected systems to improve security while minimizing resource use.
Researchers
-
systems and methods for managing data proxies
United States of America | Granted | 10,637,951
Figures
Technology
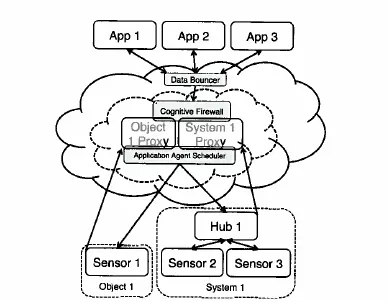
Data Proxies are a means of applying observers and estimators to generate digital duplicates of physical systems. The use of an estimator allows the reduction in sampling and transmission rate at the device and improves security by eliminating the possibility of direct connectivity between a device and an application. In the Inventors’ model, Data Proxies extend the Cloud architecture, with estimators creating interpolated approximates rather than exact mirrors of input data. The system employs an “Application Agent,” which is a query manager running in the Cloud. The Application Agent uses the meta-QoD aggregated from a Proxy’s entire application payload, and dynamically determines the most resource efficient configuration of requests.
The abstraction of physical and real devices additionally creates a network separation that allows for the use of a Cloud-run “Data Bouncer” that handles device authorization lists and chain-of-trust validation, and a Cognitive Firewall to moderate requests that might exceed control limits. The Cognitive Firewall applies the system model to validate that commands are benign, as well as examines system evolution to identify when the model breaks down, suggesting a possible system fault. This system saves bandwidth and power while improving the efficiency of the sampling system. Additionally, security is improved as the Application Agent manages update rates, connection duration and more, with the Data Bouncer shielding devices from Denial of Service (DoS) attacks and moving security to areas with improved computation powers.
Problem Addressed
The world’s devices, services, and people are increasingly interconnected. However, challenges to the creation of pervasive connectivity exist. To ensure that even resource-constrained devices can belong to interconnected systems, there is a need for a system-wide input minimization. This results in optimized systems that use computation and power where it is more available, less costly, and more easily scaled in gateway devices or in the Cloud. The Inventors’ model builds a layer of intelligent Data Proxies based on statistical and physical system models to efficiently meet prescribed Quality of Data (QoD) requirements for various applications while improving security. Additionally, a Cognitive Firewall for system protection is introduced, as well as a process framework for optimally minimizing resource requirements.
Advantages
- System offers resource reductions that enable increased connectivity while addressing consumer and industry demands for enhanced security
- System saves bandwidth and power, which contributes the loner operational life and lower operating cost for sensors in the field
- Proxies allow for temporal/spatial interpolation of data, improving time constant of system
License this technology
Interested in this technology? Connect with our experienced licensing team to initiate the process.
Sign up for technology updates
Sign up now to receive the latest updates on cutting-edge technologies and innovations.